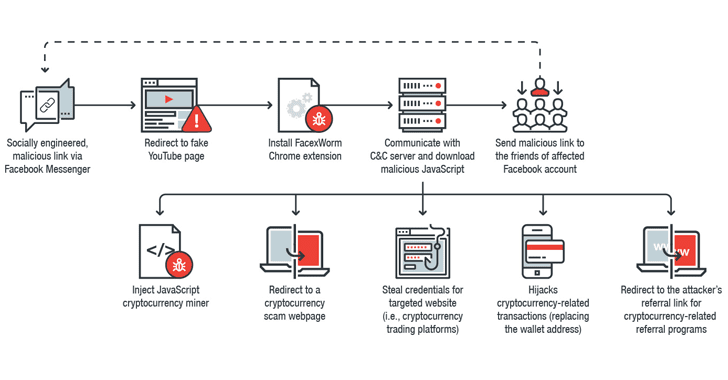
If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don’t click on it without taking a second thought.
![]()

If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don’t click on it without taking a second thought.
![]()

Facebook CEO Mark Zuckerberg will testify before Congress this week to explain how his company collects and handles users’ personal information.
The past few weeks have been difficult for Facebook over concerns that the data of millions of users has been breached.
Facebook stores details of almost every action you have taken and interaction you have engaged in on its platform.
![]()

NTFS file system is designed to work with Windows but In Mac macOS writing to NTFS volumes are impossible without additional software. There are some software which require you to pay for it, but this method is easy and free.
1- You’ll need Apple’s command line developer tools. If you haven’t installed them yet, you can open a Terminal and run the following command:
xcode-select --install
Click “Install” when you’re prompted to install the tools.
![]()
apt update && apt upgrade -y
apt-get install software-properties-common
add-apt-repository ppa:certbot/certbot
apt update && apt upgrade -y
sudo apt-get install python-certbot-apache
Add domain or subdomain name to create the certificate.
sudo certbot --apache -d smsk.biz -d www.smsk.biz
just for test renew
sudo certbot renew --dry-run
Reload apache service
/etc/init.d/apache2 reload
Add command to crontab for everyday renew.
Because you will be allowed to be renewal the day before your certificate is expire.
crontab -e
0 1 * * * sudo certbot renew --quiet
[wpedon id=”539″ align=”right”]
![]()
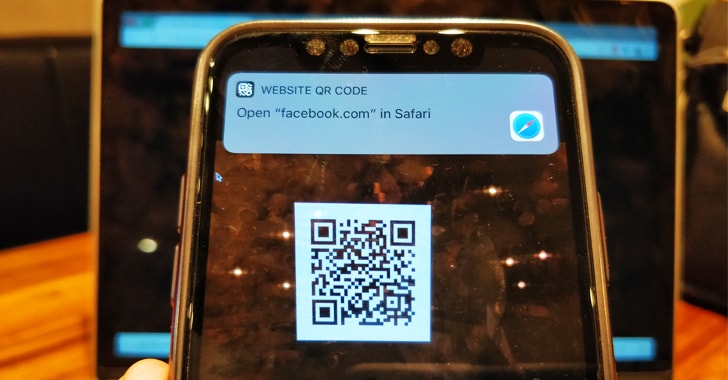
A new vulnerability has been disclosed in iOS Camera App that could be exploited to redirect users to a malicious website without their knowledge.
The vulnerability affects Apple’s latest iOS 11 mobile operating system for iPhone, iPad, and iPod touch devices and resides in the built-in QR code reader.
With iOS 11, Apple introduced a new feature that gives users ability to automatically read QR codes using their iPhone’s native camera app without requiring any third-party QR code reader app.
You need to open the Camera app on your iPhone or iPad and point the device at a QR code. If the code contains any URL, it will give you a notification with the link address, asking you to tap to visit it in Safari browser.
However, be careful — you may not be visiting the URL displayed to you, security researcher Roman Mueller discovered.
According to Mueller, the URL parser of built-in QR code reader for iOS camera app fails to detect the hostname in the URL, which allows attackers to manipulate the displayed URL in the notification, tricking users to visit malicious websites instead.
![]()
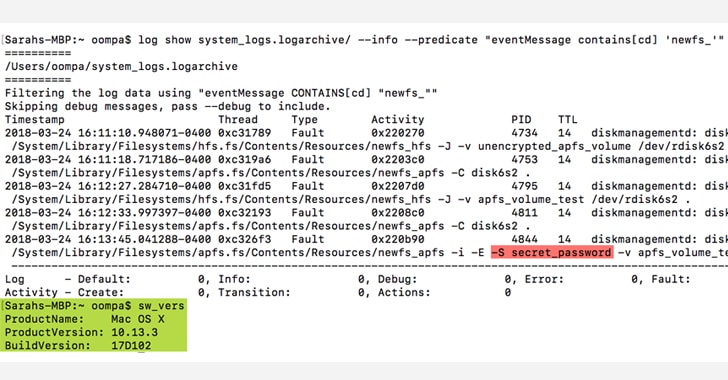
A severe programming bug has been found in APFS file system for macOS High Sierra operating system that exposes passwords of encrypted external drives in plain text.
Introduced two years ago, APFS (Apple File System) is an optimized file system for flash and SSD-based storage solutions running MacOS, iOS, tvOS or WatchOS, and promises strong encryption and better performance.
Discovered by forensic analyst Sarah Edwards, the bug leaves encryption password for a newly created APFS volume (e.g., encrypting USB drive using Disk Utility) in the unified logs in plaintext, as well as while encrypting previously created but unencrypted volumes.
“Why is this a big deal? Well, passwords stored in plaintext can be discovered by anyone with unauthorized access to your machine, and malware can collect log files as well and send them off to someone with malicious intent,” Edwards said.
![]()
Özel olarak faklı bir dosyaya yazılan loğları log sunucusuna göndermek için şu adımlar takip edilir.
Bu örnekte postgres pg_log dosyası içerisine kaydedilen loğları log sunucusuna gönderiyoruz.
Bu örnekler ilgili log dosyası kaynağı değiştirilerek ve etiketleme yapılarak çoğaltılabilir.
Önce konfigürasyon dosyamızı oluşturuyoruz.
![]()
If you want to setup this configuration you need to minimum 350Gb free disk space.
############### Server Side ###############
sudo apt-get install apache2
sudo apt-get install apt-mirror
sudo mkdir -p /Mirror/apt-mirror
sudo vi /etc/apt/mirror.list
![]()
Adding this PPA to your system
You can update your system with unsupported packages from this untrusted PPA by adding ppa:mrazavi/openvas to your system’s Software Sources.
sudo add-apt-repository ppa:mrazavi/openvas
sudo apt-get update
![]()
One of the most important feature of Nagios is the notification system; by default Nagios will use the local mail daemon (mail) to send all the notifications.
Maybe this kind of system was working fine in past, but today, with this huge amount of spam circulating all over the world, this kind of emails from a not verified source can be filtered by the same company antispam system.
In order to avoid this issue I will explain how to configure Nagios using an external smtp server also with smtp authentication.
![]()